Installing Palo Alto
This integration relies on Syslog. Logs received via Syslog are parsed and correlated by UTMStack automatically.
1. Configure your device to send logs to a UTMStack agent on ports:
- 7006 TCP
- 7006 UDP
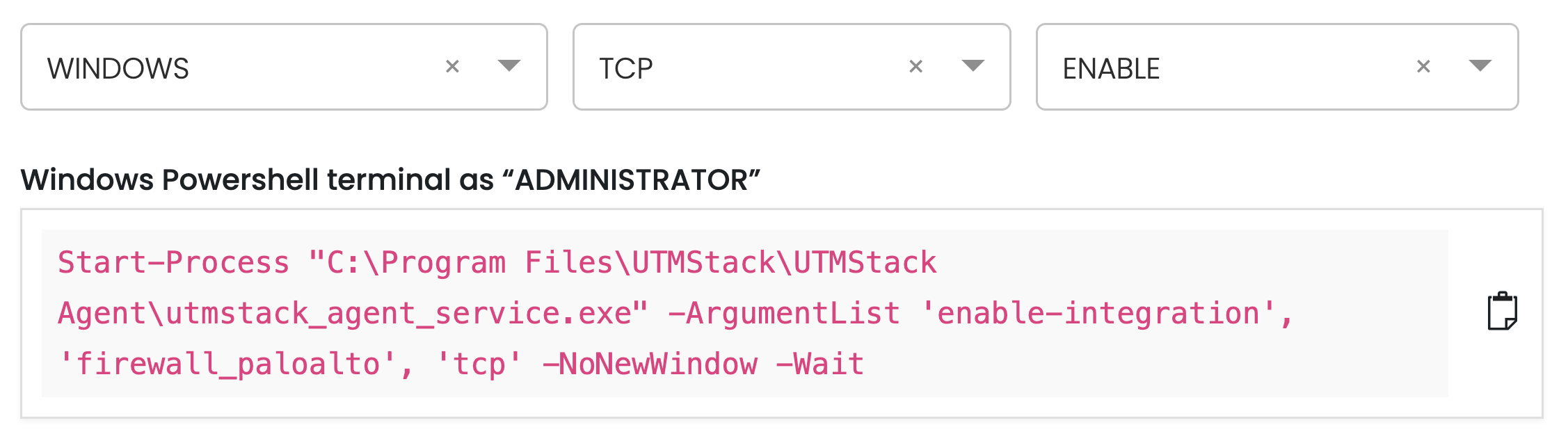
2. Enable log collector.
To enable the log collector where you have the UTMStack agent installed, follow the instructions below based on your operating system and preferred protocol.
Example: